Integrating Covert Channel Detection into an Open Source IDS
Architecture
As basis for our implementation we choose Bro (for more details on why we chose Bro refer to our tech reports). This page provides a brief overview of the architecture of our IDS extension for Bro. For more details please refer to our technical reports.
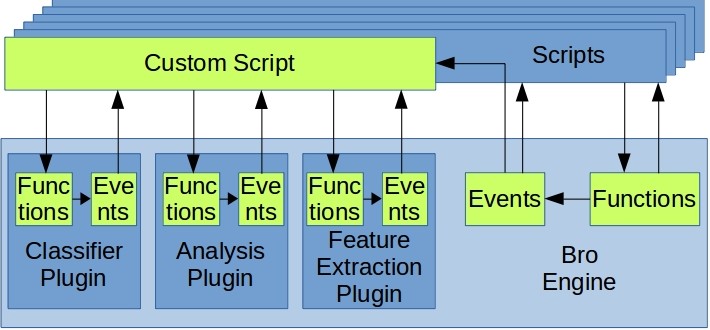
We are extending Bro with plugins to extract features and do some analysis on the extracted features. We made use of Bro's capability to add plugins and do not modify any internals of Bro. The whole infrastructure is held together by the Custom Script which manages the communication flows between our plugins internally and with Bro. To make use of our IDS extension, one needs to change the script accordingly, either by loading additional scripts from an existing script and/or by modifying an existing script.
Whenever Bro sniffs a packet from the network, it does some flow identification. The flow / connection is then passed along with the packet to be inspected, and events of interests are raised, e.g. a new_packet event for every packet, an ICMP_echo_request event whenever the packet is an ICMP packet with echo request, and so on. Bro script is event-driven, so writing event handlers for a specific event and raising events are at the heart of Bro script execution.
We have created three new types of plugins that are responsible for extracting features from the observed traffic (Feature Extraction Plugin), calculating metrics based on the extracted features (Analysis Plugin) and classifying the traffic into legitimate and covert channel based on the calculated metrics and a model of the properties of legitimate traffic and covert channels (Classifier Plugin).
Whenever feature, e.g. some header field, of interest is extracted (in the Feature Extraction Plugin), an event is raised containing the corresponding feature value. The event containing feature value (or set of features) is then handled by the Analysis Plugin. To be more precise, the event is handled by Bro script and then the value is passed to the Analysis Plugin. Once the Analysis Plugin has calculated the metric, another event may be raised which contains the value of this analysis metric. The metric values can be passed further to a classifier (such as a decision tree), or they can be handled directly in the script, e.g. an email notification can be sent when a certain threshold is violated.
Current set of features extracted
Currently implemented analysis engine
Authors: Dr Sebastian Zander e-mail: S.Zander@murdoch.edu.au | Dr Hendra Gunadi e-mail: hendra.gunadi@murdoch.edu.au
This project is supported by a grant provided by the Comcast Innovation Fund.